SaaS- Software as a Service
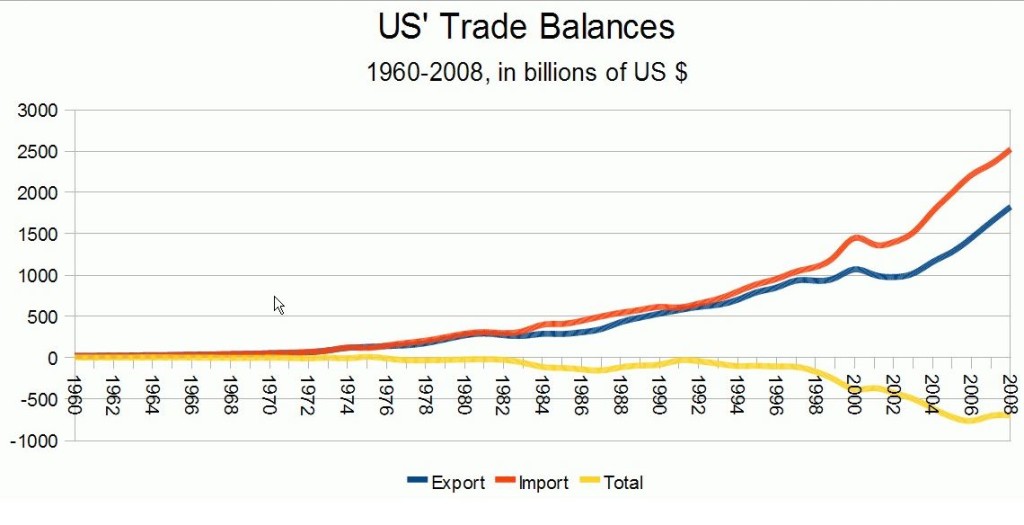
We are migrating to an economy where more of our intellectual property is embodied in digital format. The practitioners who create this intellectual property are not second class people who are undeserving of the fruits of their labor. Even though the developers who created companies like Twitter were compensated, the venture capitalists who funded this style business model are running out of money. I am aware that many of these start-ups planned an advertising funded business model. However, the available total advertising dollars available means that less than 25% of them will survive. Since the first world nations elected to offshore their manufacturing, insuring that compensation is paid for intellectual property is even more important in reversing balance of trade deficits and eventual bankruptcy.
Enter the SaaS- Software as a Service business model. We are aware that most of the creation cost of intellectual property in digital form is spent making the first copy. Our modern communication and computer technology has reduced the cost of making duplicate copies to almost nothing. This has resulted in an elimination of more than 1/2 of the revenue stream in fields like music, motion pictures and pharmaceuticals. Having seen the fruits of the efforts to create intellectual property siphoned away, prudent planners choose to insure that they will retain the fruits of their effort. “Sometimes the questions are COMPLICATED and the answers are SIMPLE” Dr Seuss Geisel. People who need food on their table and roofs over their heads cannot afford to give away the effort that funds their life. New software will only be sold as SaaS. The development effort to create the first copy will be shared by all users because it will be the only copy. Unfortunately, SaaS is too late for Windows 95, Android, Office that already have generic copies in the marketplace. It is too late to close the barn door after the horses have left. Some of the first SaaS offerings will be in Internet Security. The current system of maintaining defenses on everyone’s computer will fade. The embedded back doors in the basic computer operating systems are the problem. Once the intruders use the back doors to gain control, the first action they perform disables the defenses. Users who wish to enjoy the benefits of secure data and reliable computer operation will discover that SaaS can deliver a service that isolates them from the web hackers and dangers using encrypted links. All communication to the unprotected web will be routed through the proxy server with a resident up to the date SaaS protection program. It is very possible that it will be necessary in the short term to add Wifi or internet dongles to circumvent the unsecured communication hardware that came with the users device. I can picture the entire industry migrating back to a new variation of its roots. In the very beginning, computer users used dumb telex machines to interact with time-sharing computers that housed all of the programs and data.